In the wake of large-scale global events, cybercriminals are among the first to attempt to take advantage of the situation and seek financial gain. In February 2020, the World Health Organization (WHO) released an advisory warning of ongoing scams involving the ongoing outbreak of COVID-19 / Coronavirus. These scams aim to exploit people’s fear and uncertainty concerning the disease’s spread.
How attackers exploit the Covid-19 crisis
1. Phishing and social engineering scams
Phishing is one of, if not the single most common attack techniques. Reports of email phishing campaigns using COVID-19-related lures surfaced almost immediately after confirmed infections began increasing in January 2020. Health organizations such as the WHO and US Centers for Disease Control and Prevention (CDC) have been prime targets for impersonation due to their perceived authority: Attackers have been observed tempting victims with URLs or document downloads using promises of important safety documentation or infection maps.
COVID-19 has also been a popular topic of discussion on cybercriminal forums. For example, in February 2020, a user initiated a thread on the prestigious Russian-language cybercriminal forum XSS to advertise a new COVID-19-themed phishing scheme. The user advertised a method to deliver malware via an email attachment disguised as a distribution map of the virus’s outbreak, containing real-time data from the WHO. The map itself is an impersonation of a legitimate map created by the Johns Hopkins Center for Systems Science and Engineering (CSSE). The offering was priced at $200 for a “private build”, and if buyers also required a Java CodeSign certificate, the price would be $700.
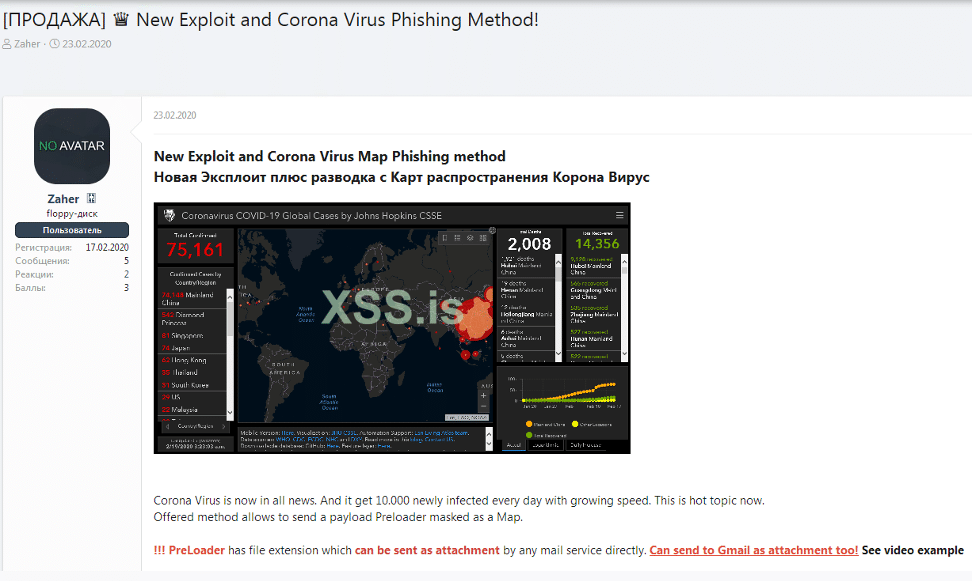
XSS post on COVID-19-related phishing scam
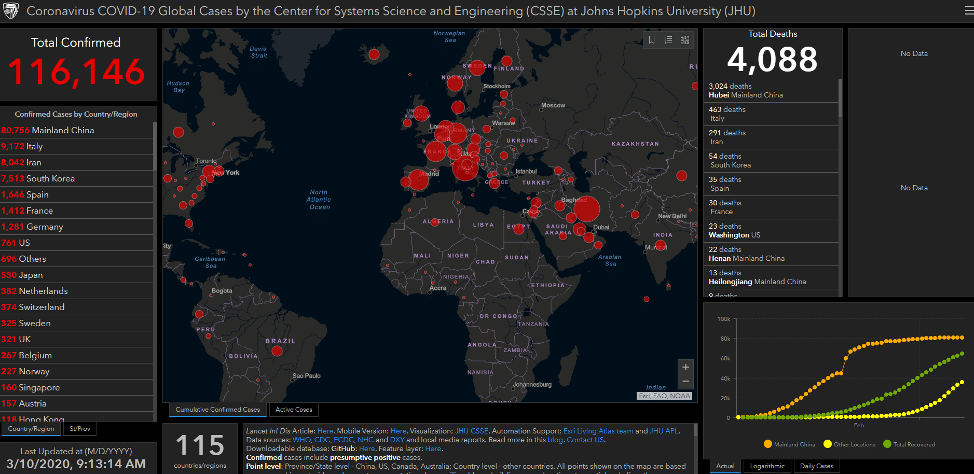
Legitimate Johns Hopkins COVID-19 distribution map
Another phishing scam, as detailed by Sophos, impersonated an official email correspondence from the WHO. The email contained a link to purported document on preventing the spread of the virus, but redirected victims to a malicious domain which attempted to harvest credentials. The email contained several grammatical and format errors, which can be used by attackers to narrow down their victims and bypass spam filters.
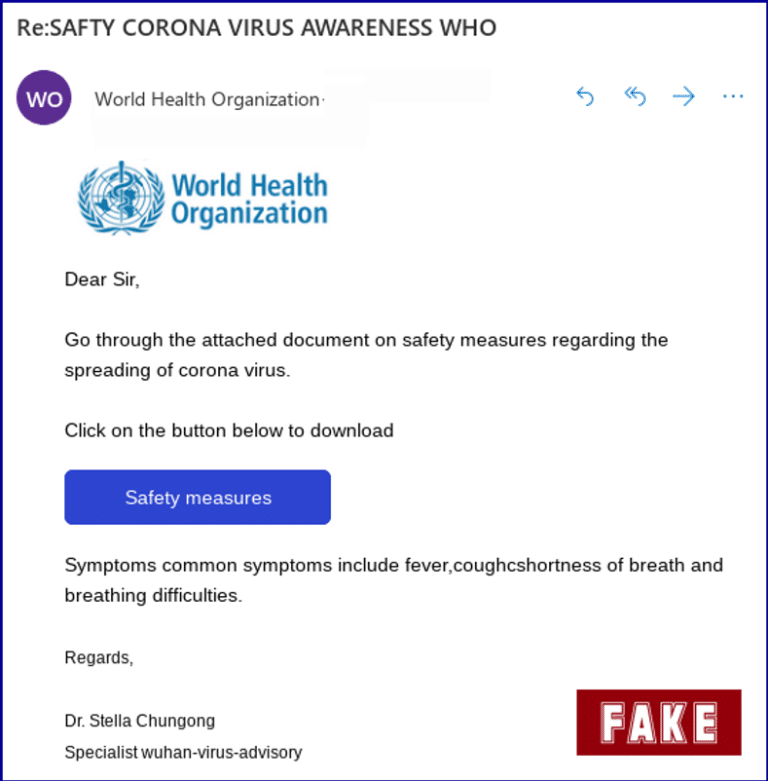
Phishing scam impersonating the WHO (Source: Sophos)
Organizations like the WHO or CDC are also not the only ones at risk of being impersonated. Since January 2020, the number of COVID-19-related domains registered has increased significantly: Digital Shadows has identified over 1,400 domains registered over the past three months. While many of these are likely legitimate and dedicated to providing information on the virus and its spread, it is almost certain that a portion have been created with malicious intent. Malicious domains can be used to spread misinformation, host phishing pages, impersonate legitimate brands, and sell fraudulent or counterfeit items. In March 2020, the UK’s National Fraud Intelligence Bureau (NFIB) reported over 21 cases of COVID-19-related fraud schemes, resulting in losses of over £800,000 in the UK alone. The NFIB cited specific examples which included the fraudulent sale of face masks and sites which promised victims a map of COVID-19 infections near them in return for a bitcoin payment.
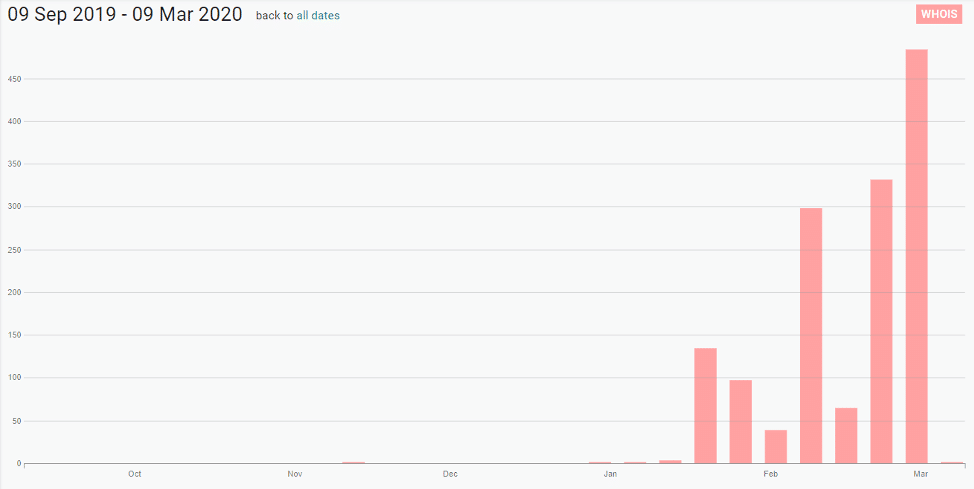
COVID-19-related domains registered over the past six months (Source: Digital Shadows’ Shadow Search)
2. Malicious apps
Although Apple has placed limits on Covid-19-related apps in its App Store and Google has removed some apps from the Play store, malicious apps can still pose a threat to users.
DomainTools uncovered a site that urged users to download an Android app that provides tracking and statistical information about Covid-19, including heat map visuals.
However, the app is actually loaded with an Android-targeting ransomware now known as CovidLock. The ransom note demands $100 in bitcoin in 48 hours and threatens to erase your contacts, pictures and videos, as well as your phone's memory. An unlock token has reportedly been discovered.
DomainTools reported the domains associated with CovidLock were previously used for distributing porn-related malware. “The long run history of that campaign, now looking disabled, suggests that this Covid-19 scam is a new venture and experiment for the actor behind this malware,” said Tarik Saleh, senior security engineer and malware researcher at DomainTools, in a blog post.
Proofpoint also discovered a campaignsha asking users to donate their computing power a la SETI@Home but dedicated to Covid-19 research, only to deliver information-stealing malware delivered via BitBucket.
3. Insecure endpoints and end users
With large numbers of employees or even the entire businesses working remotely for an extended time, the risks around endpoints and the people that use them increase. Devices that staff use at home could become more vulnerable if employees fail to update their systems regularly.
Working from home for long periods of time may also encourage users to download shadow applications onto devices or flout policies they would normally follow in the office.
The International Association of Information Technology Asset Managers recommends that all IT assets being taken home be signed out and tracked, that companies provide policy and advice around how assets be used at home (especially if people are used to sharing devices with family), remind users of policies around connecting to public WiFi, and make sure they continue to update their software as needed.
4. Vulnerabilities at vendors and third parties
Every partner, customer and service provider in your ecosystem is likely going through all the same issues as your organisation. Liaise with critical parts of your third-party ecosystem to ensure they are taking measures to secure their remote workforce.
Security priorities for remote working at scale
Liviu Arsene, global cyber security researcher at Bitdefender, recommends that organisations take the following steps to ensure secure and stable remote working:
- Bump up the number of simultaneous VPN connections to accommodate all remote employees
- Set up and support conferencing software that ensures both a stable voice and video connection
- Ensure all employees have valid credentials that don’t expire within less than 30 days as changing expired Active Directory credentials can be difficult when remote
- Send out rules and guidelines regarding accepted applications and collaborative platforms so employees are aware of what is sanctioned and supported and what is not
- Have gradual rollout procedures for deploying updates, as delivering them all at once to VPN-connected employees could create bandwidth congestions and affect inbound and outbound traffic
- Enable disk encryption for all endpoints to reduce the risk of data loss on compromised devices













